To make signing in to Received Digital easy and secure for your users, Received Digital supports single sign-on (SSO) with any SAML 2.0 identity provider.
Below, you’ll find instructions for setting up SSO with Okta and Microsoft Entra, though the process will look similar for any SAML 2.0 identity provider.
To complete the setup process, you’ll need access to your identity provider account. You’ll also need to know your company’s Received Digital subdomain. See the instructions below to find this information.
Finding your company's Received Digital subdomain
To find your company’s Received Digital subdomain …
- Log in to Received Digital.
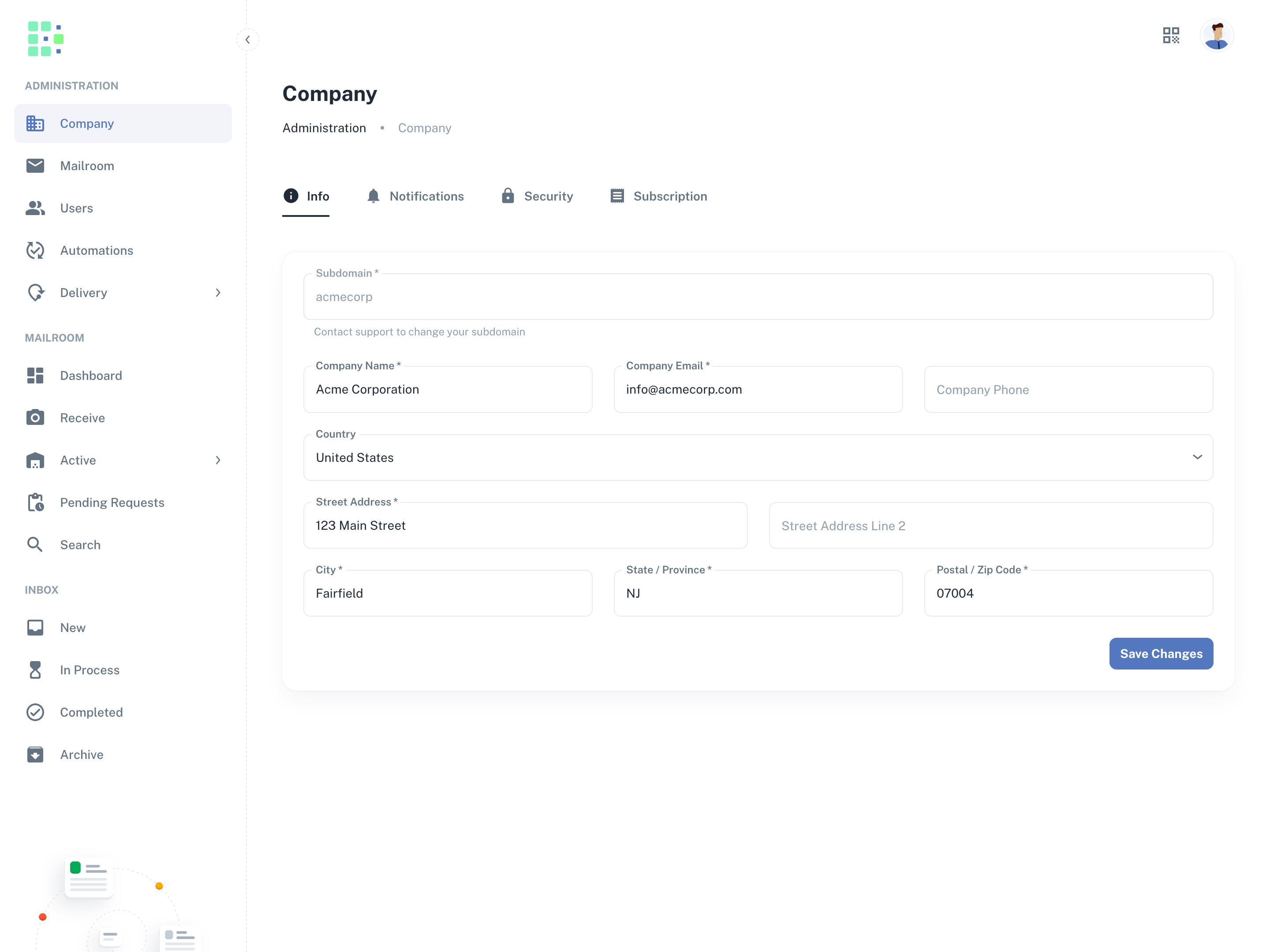
- Under the Administration section in the left menu, click Company.
- Find your company’s subdomain in the first field at the top.
Setting up SSO with Okta
To get started, log in to your Okta admin account.
Create a new app integration
Create a new app integration for Received Digital:
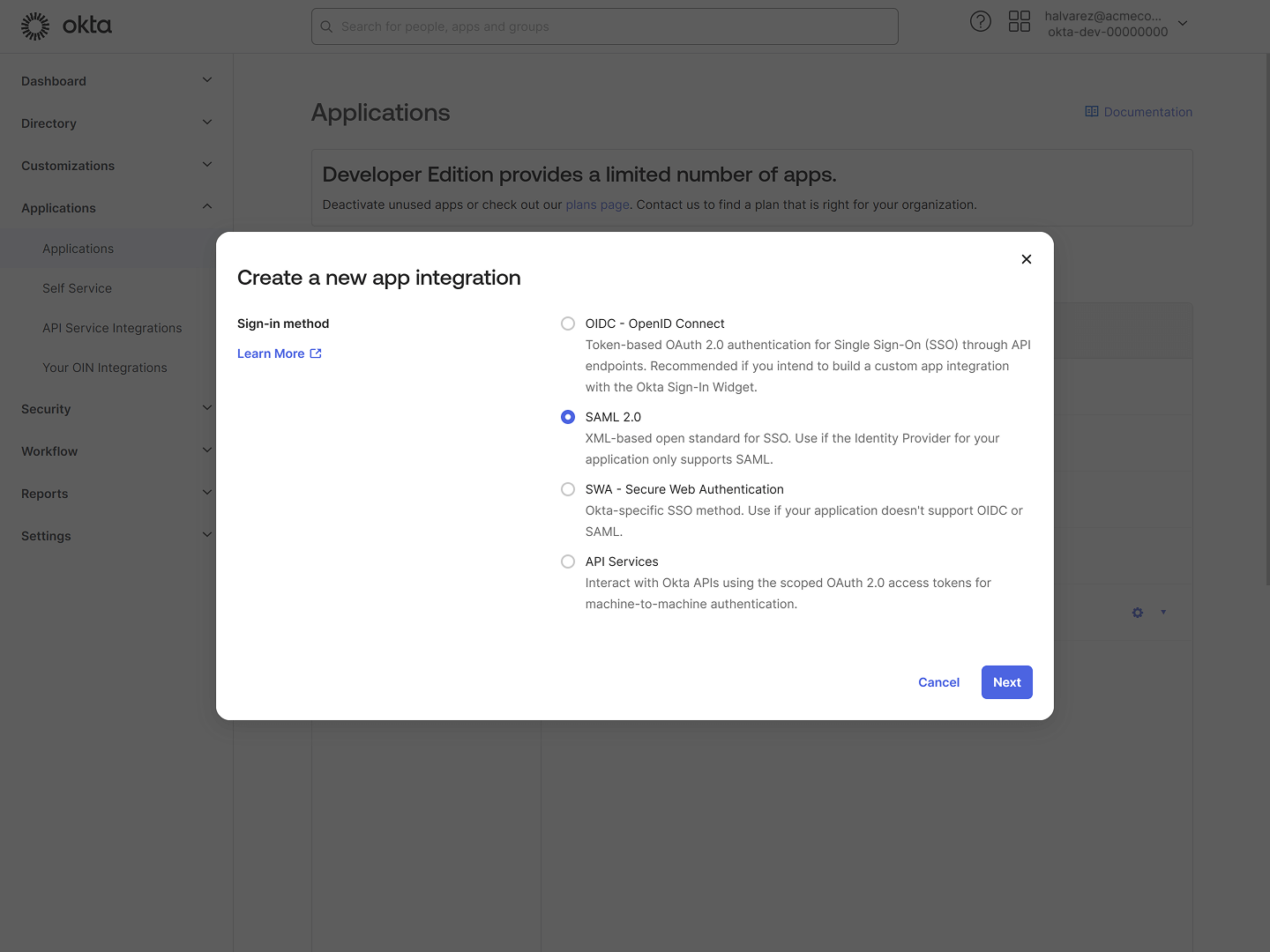
- In the left menu, expand the Applications group, and click Applications.
- Click the Create App Integration button above the table.
- In the dialog that appears, select SAML 2.0.
- Click Next.
Enter general settings
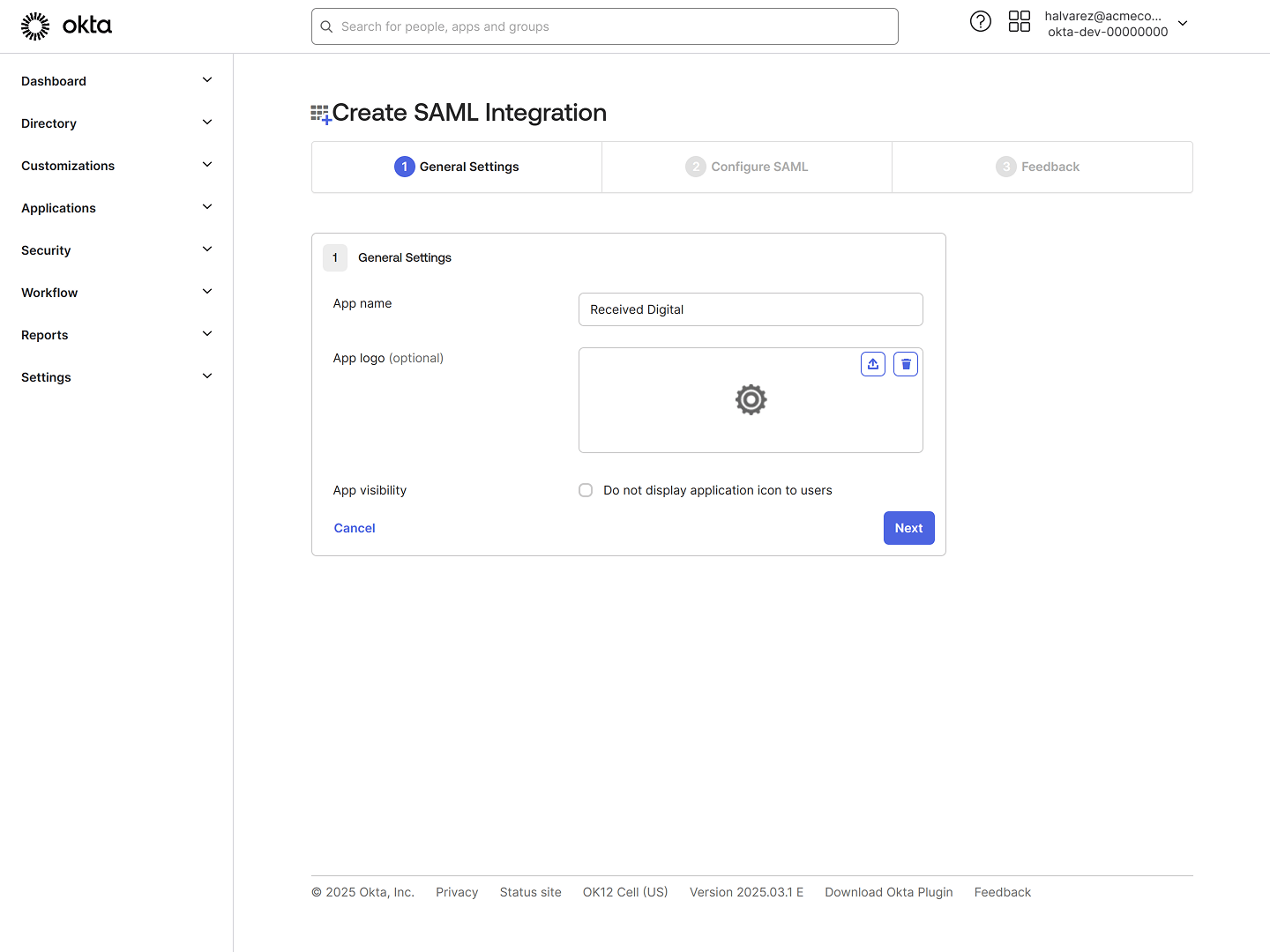
- In the App Name field, enter a name for the app integration, such as Received Digital.
- Click Next.
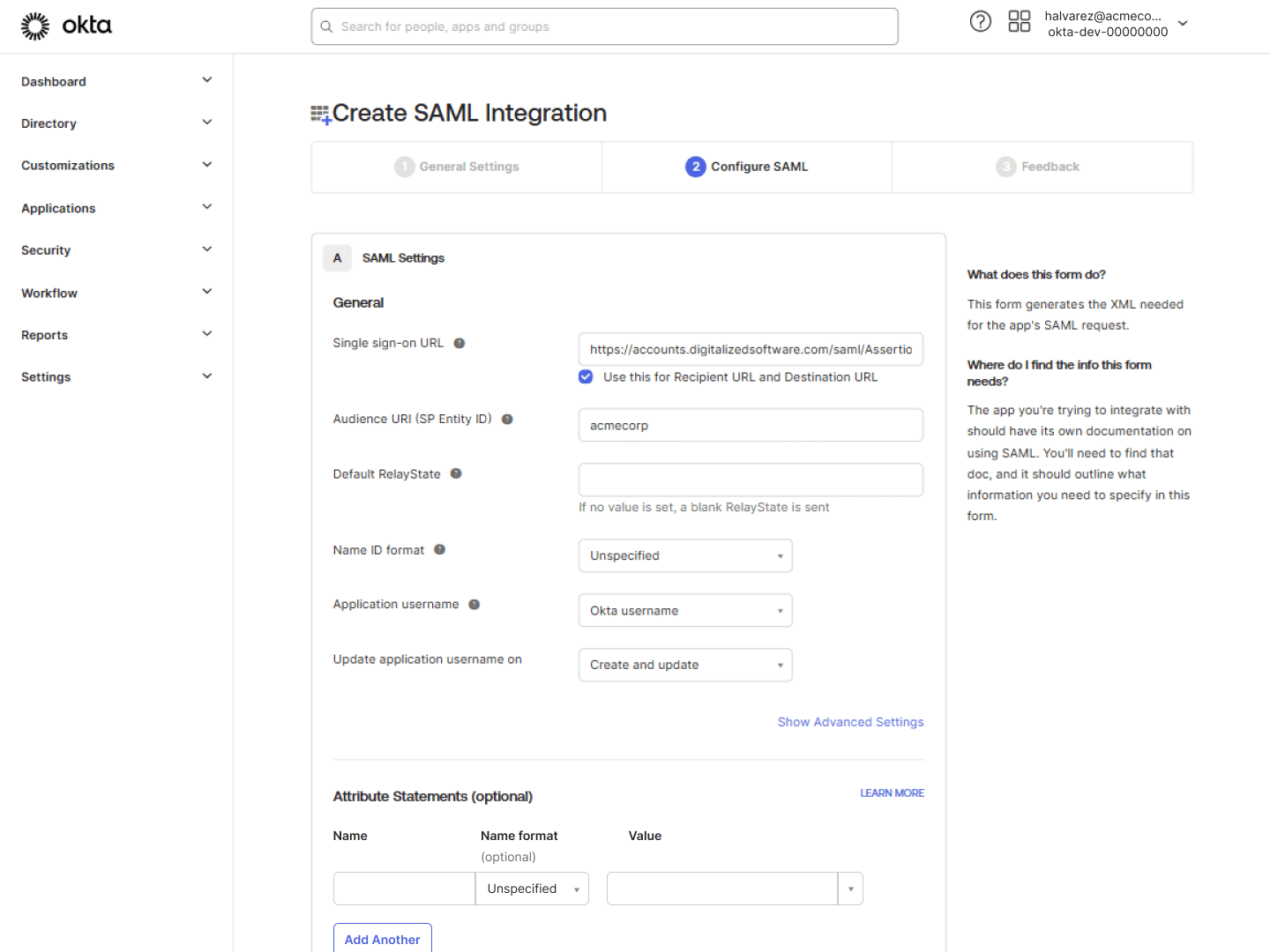
Enter SAML settings
- In the Single Sign-On URL field, paste this URL:
https://accounts.digitalizedsoftware.com/saml/AssertionConsumerService
- In the Audience URI (SP Entity ID) field, enter your company’s Received Digital subdomain.
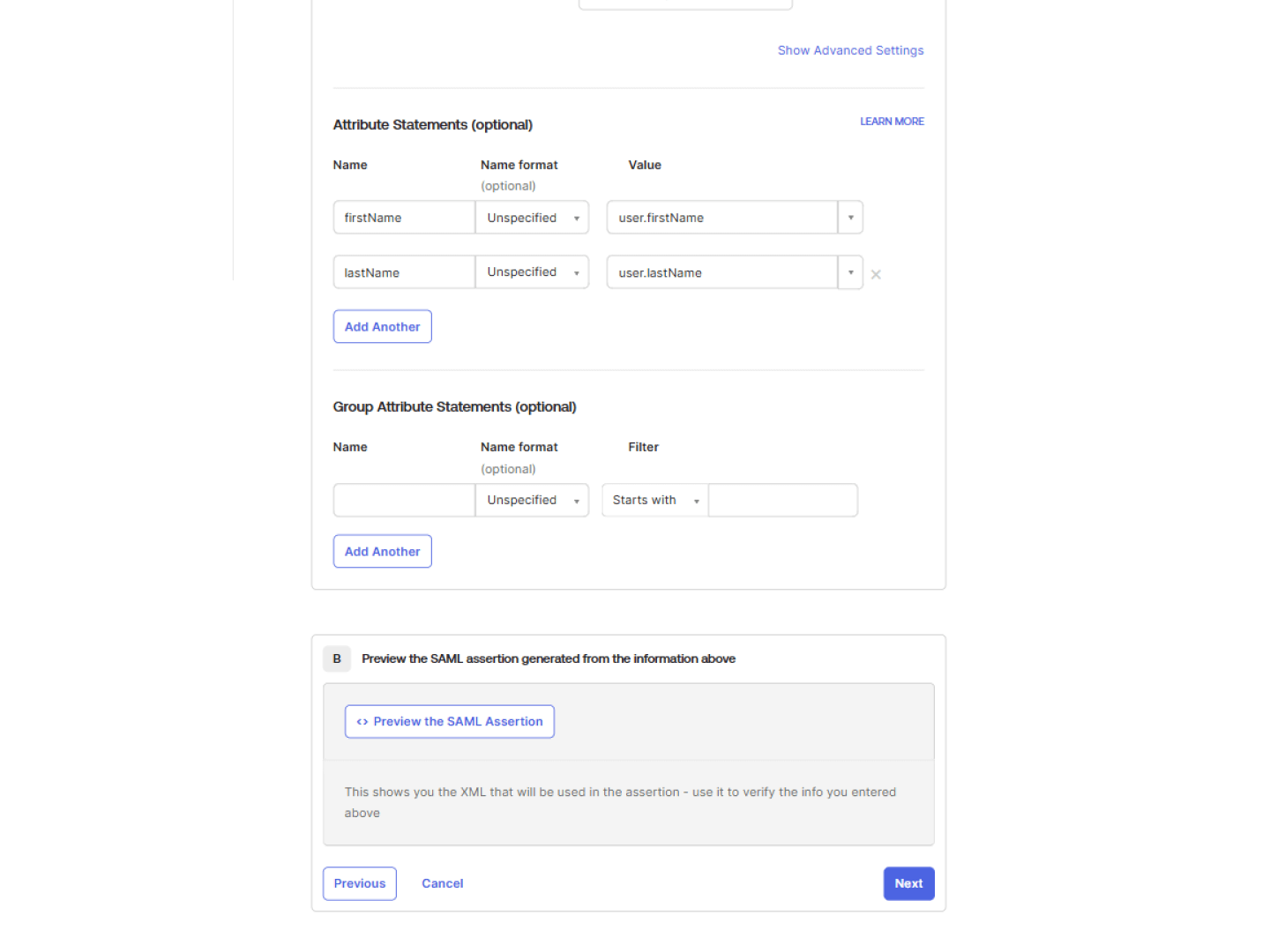
Add attribute statements
Next, add two attribute statements:
- For the first, enter firstName for the name and select user.firstName from the dropdown for the value.
- For the second, enter lastName for the name and select user.lastName from the dropdown for the value.
Copy metadata URL
- Proceed to the end of the setup.
- Copy the Metadata URL provided on the completion screen.
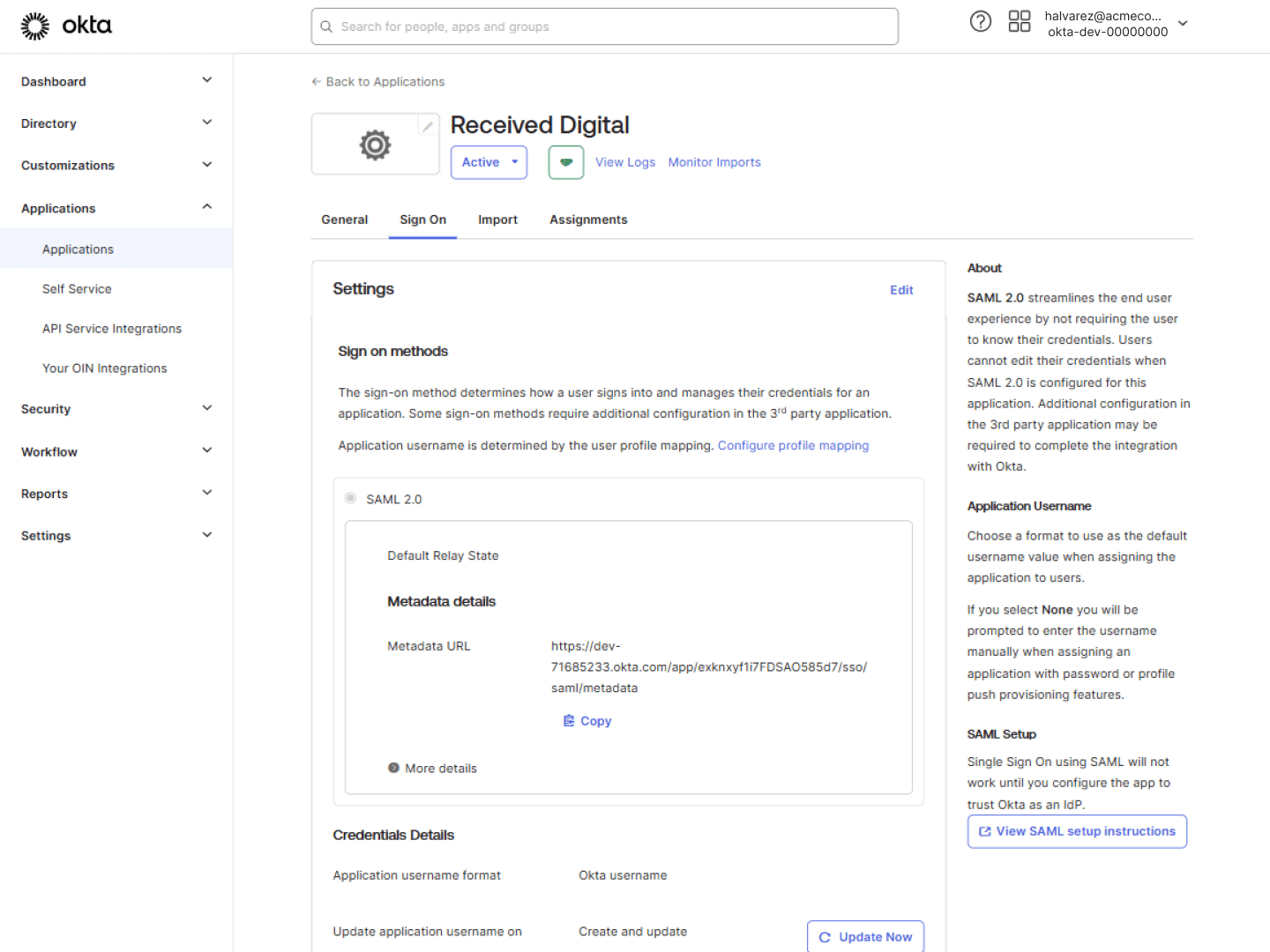
Configure SSO in Received Digital
Navigate back to Received Digital to complete the process:
- Under the Administration section in the left menu, click Company.
- Navigate to the Security tab.
- In the Single Sign-On (SSO) section, enable single sign-on by toggling the switch on.
- Paste your Metadata URL into the Identity Provider Metadata URL field.
- Click Save Changes.
With SSO configured, a new button will appear on the login page above the regular credential fields that allows users to log in with SSO.
Setting up SSO with Microsoft Entra
To get started, log in to your Microsoft Entra admin center.
Create a new application
To create a new application …
- Under the Entra ID section in the left menu, click Enterprise apps.
- Click New application at the top.
- In the search box, enter Microsoft Entra SAML Toolkit and select it from the list.
- In the drawer that opens from the right, give the application a name, such as Microsoft Entra SAML Toolkit – Received Digital.
- Click Create at the bottom.
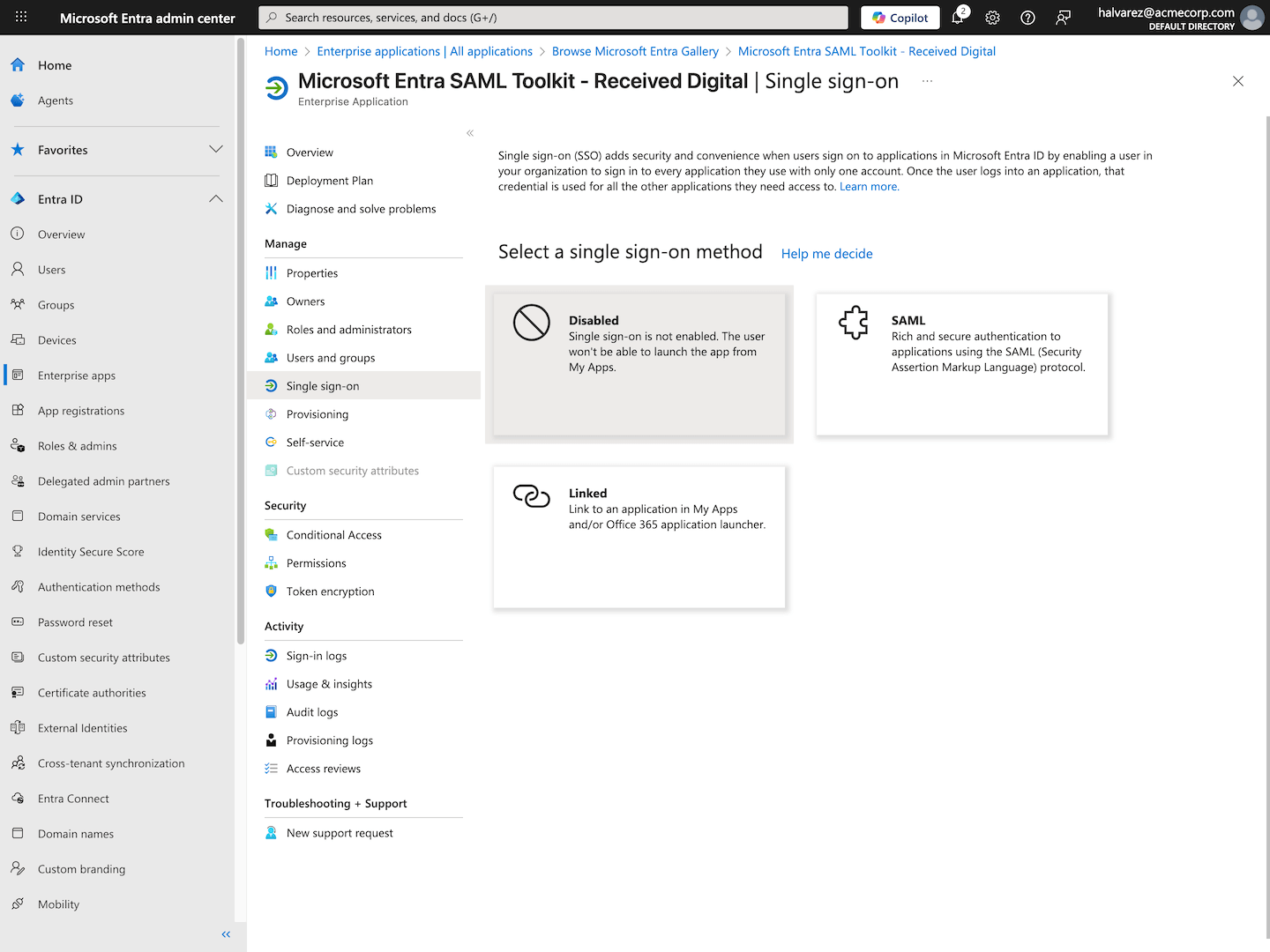
Select a single sign-on method
- Under the Manage section on the left, click Single sign-on.
- Select SAML from the list of single sign-on modes.
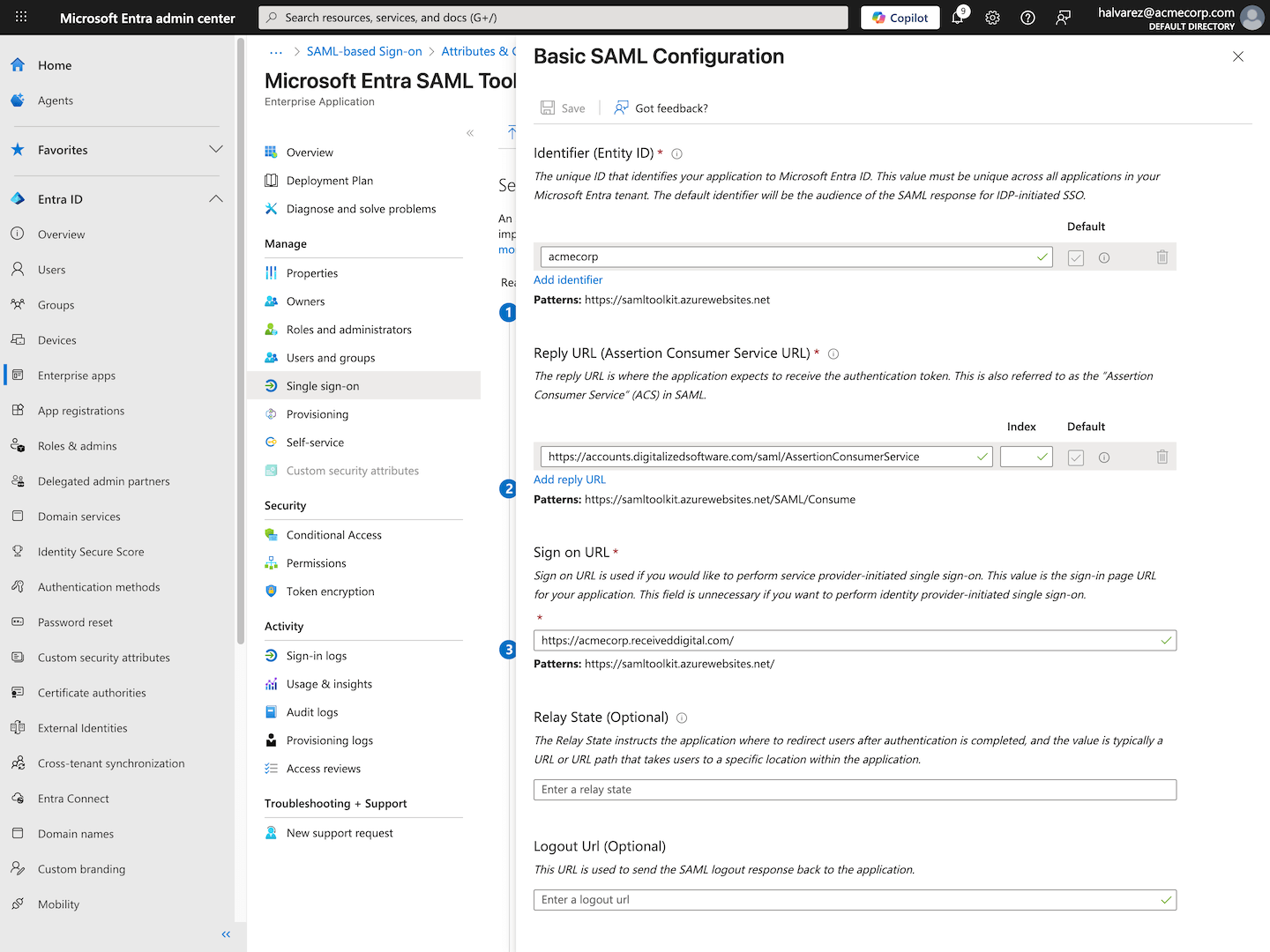
Edit Basic SAML Configuration
- In the Basic SAML Configuration section, click Edit.
- In the Identifier (Entity ID) field, enter your company’s Received Digital subdomain.
- Under Reply URL (Assertion Consumer Service URL), click Add reply URL, and paste this URL into the field that appears:
https://accounts.digitalizedsoftware.com/saml/AssertionConsumerService
- In the Sign on URL field, paste the URL below, and replace “subdomain” with your company’s Received Digital subdomain:
https://subdomain.receiveddigital.com/
- Click Save at the top, and close the drawer.
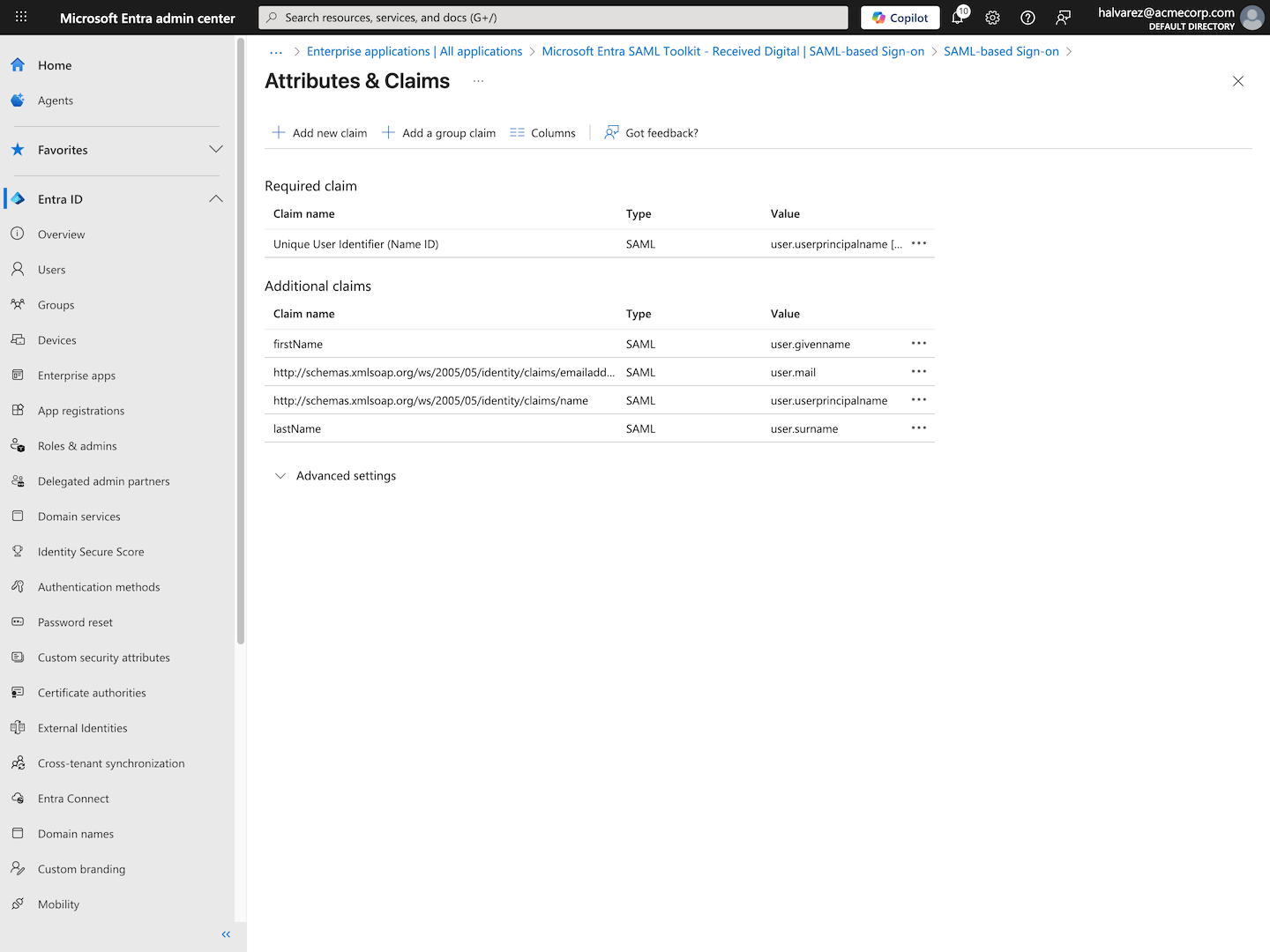
Edit Attributes & Claims
- In the Attributes & Claims section, click Edit.
- Under Additional Claims, find the row with the value user.givenname, and click on it to edit it.
- Change its name to firstName and remove the value in the Namespace field.
- Click Save.
- Next, find the row with the value user.surname, and click on it to edit it.
- Change its name to lastName and remove the value in the Namespace field.
- Click Save.
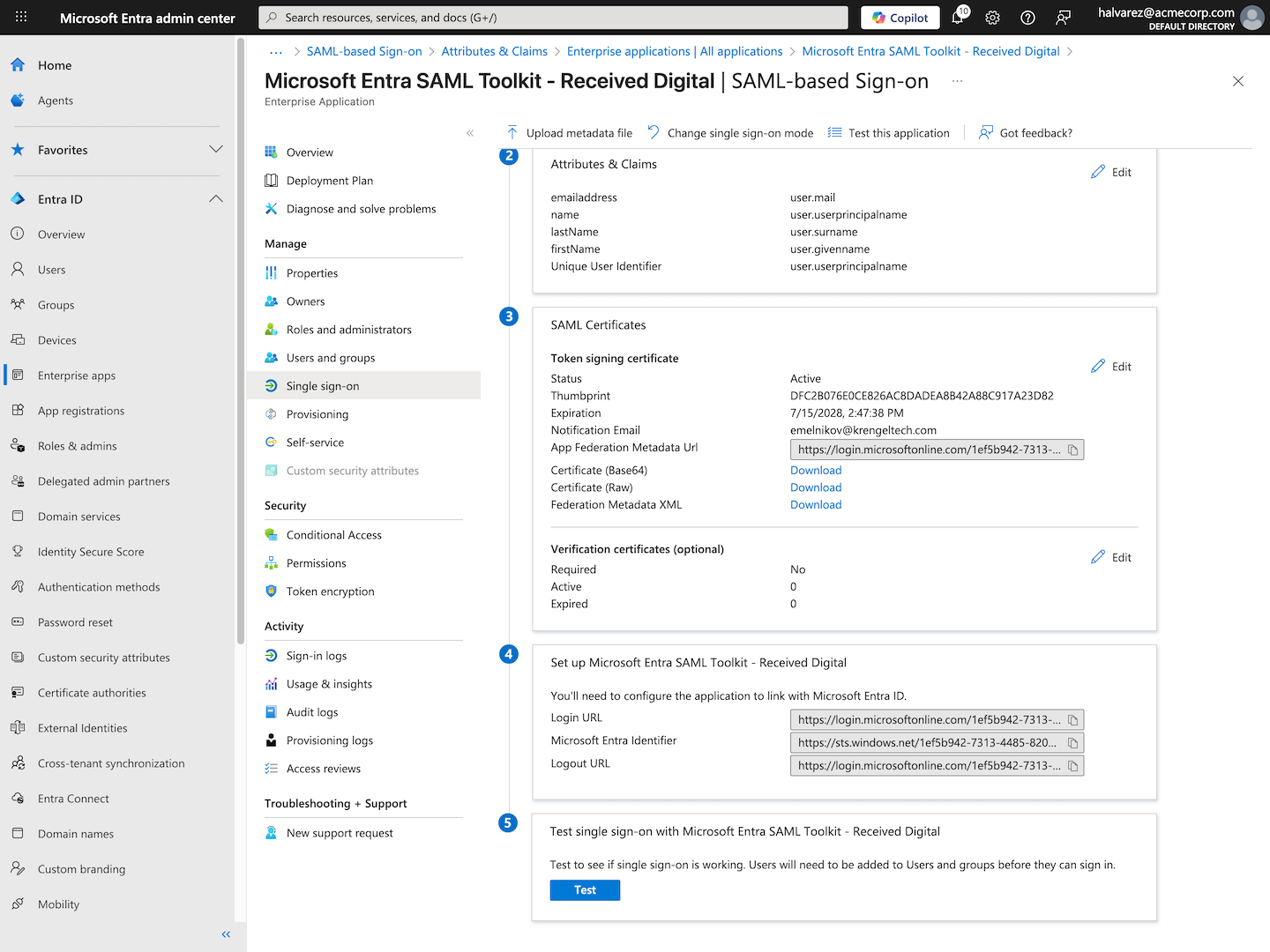
Copy app federation metadata URL
- Navigate back by clicking the close icon in the top right, then scroll down to the SAML Certificates section.
- Copy the App Federation Metadata Url.
Configure SSO in Received Digital
Navigate back to Received Digital to complete the process:
- Under the Administration section in the left menu, click Company.
- Navigate to the Security tab.
- In the Single Sign-On (SSO) section, enable single sign-on by toggling the switch on.
- Paste your App Federation Metadata Url into the Identity Provider Metadata URL field.
- Click Save Changes.
With SSO configured, a new button will appear on the login page above the regular credential fields that allows users to log in with SSO.